precision casting components,precision die casting,aluminium die casting mold,aluminium casting mold Shenzhen Kangneng Fusheng Die Casting Products Co., Ltd. , https://www.kesdiecast.com
Iran has faced a second round of cyber warfare. Virus attacks Recently, a number of international computer virus prevention and control agencies issued warnings. They found that a powerful network virus "Flame" is spreading in the Middle East. Among them, Iran is most affected by the virus. The purpose of the new network virus is to collect key information from the Iranian oil industry factory business to match the ongoing oil war against Iran.
Research shows that the "Flame" virus exploits Windows operating system vulnerabilities and can spread through local area networks, print networks, and USB interfaces. This virus presents part of the characteristics of Trojan horses and worms and does not interrupt the end system. Its purpose is to collect information. It is actually a toolkit. When the computer is infected with the original "flame" virus, the computer will be installed with a specific task module. These specific task modules can capture keyboard taps, steal passwords, delete hard disk data, automatically capture screen information, activate voice systems to eavesdrop on Internet telephony and chat content, and even use Bluetooth to steal smartphones and tablets connected to infected computers. Content. Then the stolen data is sent to the server that remotely manipulates the virus. Virus writers use about 80 servers in North America, Europe, and Asia to manipulate viruses. Once the data collection task is completed, these viruses can destroy themselves and leave no trace. Measured in terms of complexity and functional potency, the new "flame" virus emerged from more than any known computer virus. "Fire" is a dangerous spy tool that can be used to attack critical infrastructure. Although Iran announced that the virus was discovered and effectively contained, as early as April of this year, the flame virus stole a large amount of information on the Iranian oil industry factory enterprise system, and oil exports contributed 800% of Iran’s fiscal revenue, which is crucial to the economy. .
As a precautionary measure, an in-depth defense system was established at an early date. In order to ensure national economic security and strengthen the information security of industrial control systems, the Ministry of Industry and Information Technology issued the “Notice on Strengthening Information Security Management of Industrial Control Systems†(Ministry of Industry and Information Technology [2011] No. 451) in September 2011. . The notice pointed out that industrial control systems are widely used in industries such as industry, energy, transportation, water conservancy, and municipal administration to control the operation of production equipment. Once loopholes in information security of industrial control systems occur, it will cause major hidden dangers to industrial production operations and national economic security. With the development of computer and network technologies, especially the deep integration of information and industrialization and the rapid development of the Internet of Things, industrial control system products increasingly use common protocols, general-purpose hardware and general-purpose software, and various methods and the Internet. Public network connections, threats such as viruses and Trojans are spreading to industrial control systems, and the problem of information security in industrial control systems has become increasingly prominent.
In order to improve the information security of industrial control systems and their industrial communication networks, the International Electrotechnical Commission has developed IEC62443 "Network and System Information Security for Industrial Process Measurement and Control" international standards in terms of technology and management. Standards stipulate industrial control. The system is divided into five layers, and each layer must adopt information security protection measures to form a multi-layer distributed defense-in-depth defense architecture, as shown in Figure 1. From the figure, at the 5th (enterprise) level, the factory enterprise firewall is used to protect the entire enterprise against Internet security threats; at the 3/4 (monitoring) level, the management layer has a firewall with a DMZ isolation zone to the control system. Used to protect the entire control system; at the 1/2 (field device) layer, distributed security components are used to protect critical equipment such as PLCs or DCSs. 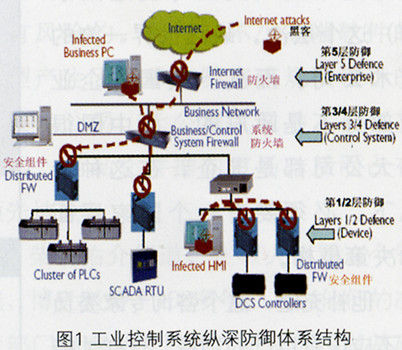
Based on the concept of the above-mentioned information security standard, the German company Phoenix Contact developed the FLMGUARD industrial information security component that can be used in such a distributed architecture, which protects part of the system network, each production unit or a single automation device. The FLMGUARD platform is a stand-alone system that can be integrated directly into industrial computers connected to industrial networks, and can be integrated in the form of PC badges if required. The implementation of hardware-based security protocols for industrial information security components does not require modification of the computer's configuration nor regular software upgrades. Compared to the processor and operating system used by the protected system, it is a completely independent system. It will have a negative impact on the system.
Since the distributed security system architecture used is to assign its own industrial information security component to each industrial system's central computer, control computer, or production robot, it has an independent level of security and specifically configures access rights and other aspects. Central management functions. The industrial information security component uses the same IP address of the computer it is protecting, so it will not be identified by the intruder, making it difficult to discover, thereby avoiding subsequent attacks. At the same time, the component is equipped with a Kaspersky Lab technology-based virus scanner for monitoring data sources to identify viruses (such as HTTP, SMTP, and FTP) in the protocol, allowing the industrial automation system to fully defend against DOS, DDOS, and network virus attacks.
At present, some countries are conducting research on offensive and defensive two types of cyber warfare systems. China should take preventive measures. In accordance with international standards, strictly follow the requirements of international standards for factories and enterprises in the information security construction, that is, according to the needs of business development, clarify the risk status and security needs, establish a blueprint for the enterprise information security framework and building a roadmap, according to The actual situation and the need to select the appropriate safety function components. From the technical point of view of implementing system security protection, factories and enterprises should set up multiple security lines to improve the system's intrusion detection capabilities, event response capabilities and rapid recovery capabilities, and form a comprehensive, three-dimensional network security technology protection system, making industrial control in key areas. System information security goes deep into defense.
Precision casting components cover various types of electronic device products, including decorative die casting, instrument casing, signal generator casing, facial recognition casing, shielding cover aluminum alloy die casting, router casing, recorder casing, air conditioning bracket die casting, military intercom casing, keyboard casing, mechanical arm accessories, electronic cigarette accessories, laptop counterweight, ATM keyboard casing, and other electronic device aluminium die casting mold products, all of which can be sent for consultation aluminium casting mol processing precision die casting.
As we all know, in June 2010 Iranian Bushehr nuclear power plant was attacked by the “Stuxnet†virus. This virus exploited the vulnerability of Wmdows operating system and spread through USB to attack the foundations of water supply and power generation designed and manufactured by Siemens. The industrial control system of the facility, after extensive analysis of data, found that the Seismic Network worm was able to find the control system of the target facility and was only activated in the designated industrial control system to control the nuclear power facilities under attack. In the worst case of the operation of cooling systems or turbines, viruses can control key processes and open up a series of execution procedures, which can cause the facilities to run out of control and eventually lead to the destruction of the entire system. Because the target of this Stuxnet virus is to attack nuclear power plants, it is described as global. The first "computer super weapon" or "network bomb" was affected by the "stuxent" virus. In August of the same year, a series of failures occurred after the opening of the Iranian Bushehr nuclear power plant. However, as a result of early detection and prompt action, it did not result in Serious consequences, but the "Stokes" virus incident, It has fully reflected that the information security of industrial control systems is facing a grim situation.